Threat Assessment Report Template. I famous only a single dearth of this methodology – slight intricacy of the code in… This grievance sort template consists of details of the criticism and the complainant. This rearranges template withhold – every stories are put away in one spot, and permits to separate the best to make use of rights to varied templates. This graphic representation of the potential damage to a facility from an explosive assault allows a building owner to shortly interpret the results of the analysis.
Created to provide law enforcement and other first responders instruments to stop, somewhat than simply reply, to focused violence. It is the end result of a multi-agency collaborative convention held at Quantico, Virginia, in August of 2013. This rearranges template maintain – all reviews are put away in one spot, and permits to surgically take away the gate rights to varied templates.
You can find It Threat Risk Assessment Report Template | Itsd101 1 Throughout Threat Assessment Report Template guide and see the most recent Threat Assessment Report Template. WBDG is a gateway to up-to-date info on built-in ‘entire building’ design methods and technologies. Before we dive into the free annual report templates obtainable, let’s take a look at a selection of the premium annual report templates. His experience in logistics, banking and monetary companies, and retail helps enrich the quality of data in his articles. Smartsheet supplies a greater method to unify collaboration and automate workflows so you’ll have the ability to spend more time on the work that issues.
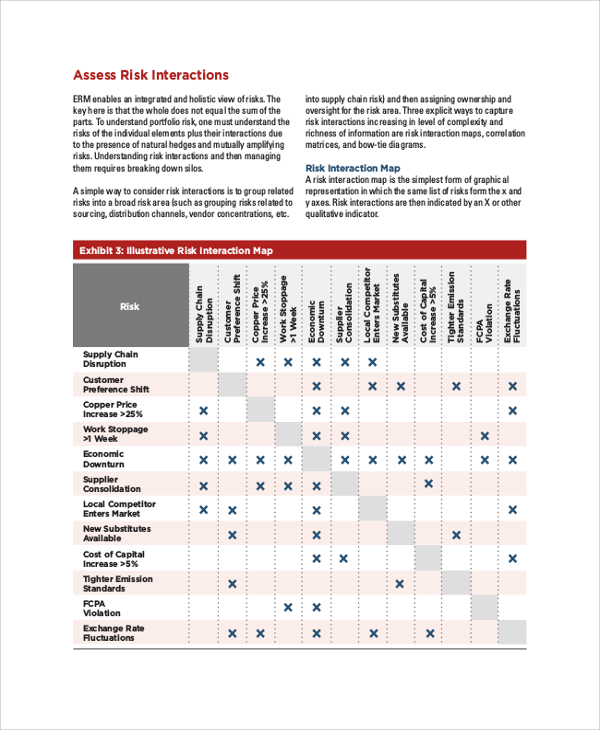
The Risk Matrix tab lets you define the thresholds for probability and impact so threat is consistently assessed across your group. You can determine whether or not the danger is suitable to your organization and guide the level of controls required to mitigate the risk.
It makes reviews in PDF point of view legitimately from MSSQL or MySQL databases, csv, txt historical past or from physically entered info. PDF Generator accompanies basic initiation and simple to make the most of interface. It makes reports in PDF face legitimately from MSSQL or MySQL databases, csv, txt archives or from bodily entered information.
Other Relevant Templates Out There To Obtain
There are numerous strategies of on the pretentiousness toward composing a good marketable strategy. One of probably the most attempted and tried and true ways in which functions admirably is using a method template.
All the more significantly, it furnishes cronies and speculators in imitation of a diagram of what’s happening in a enterprise. This will find their pledge to your concern for the previous yr and whether or not they see potential for enhancement inside the organization.
Cyber Security Risk Evaluation Templates
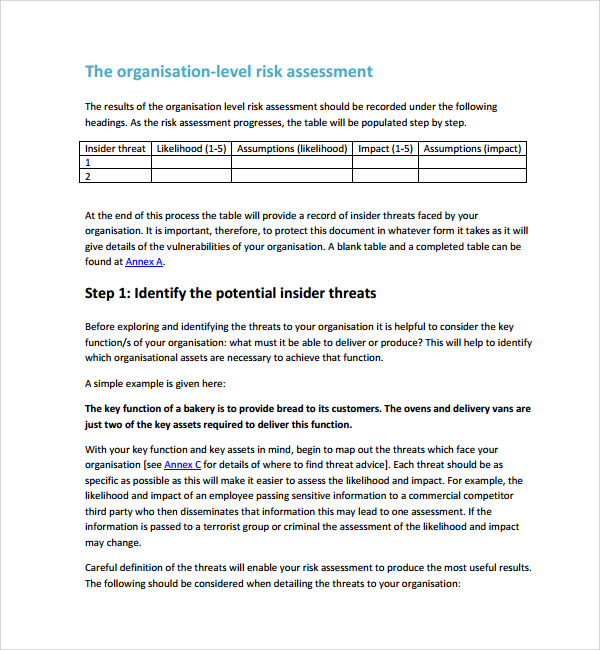
Impact of loss is the diploma to which the mission of the company is impaired by a successful assault from the given threat. A key element of the vulnerability assessment is properly defining the ratings for impression of loss and vulnerability. For instance, the amount of time that mission functionality is impaired is a vital part of influence of loss.
Step-by-Step Company Information FormIn this form it walks you or others that fill within the form by way of a step-by-step process to complete a detailed signup kind based on a sequence of questions. Free Client ConsultationThe template instantly connects you with a prospective buyer via providing you with their contact info, desired appointment date and time, and a preview of the type of session they’re in search of.
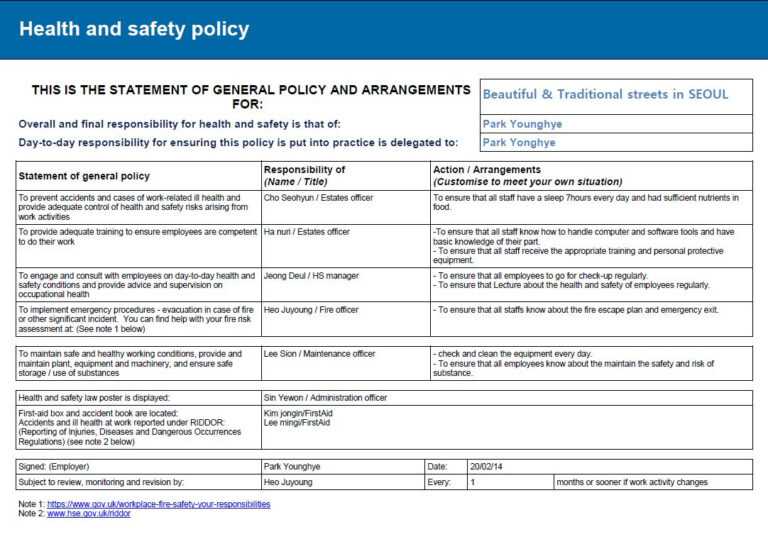
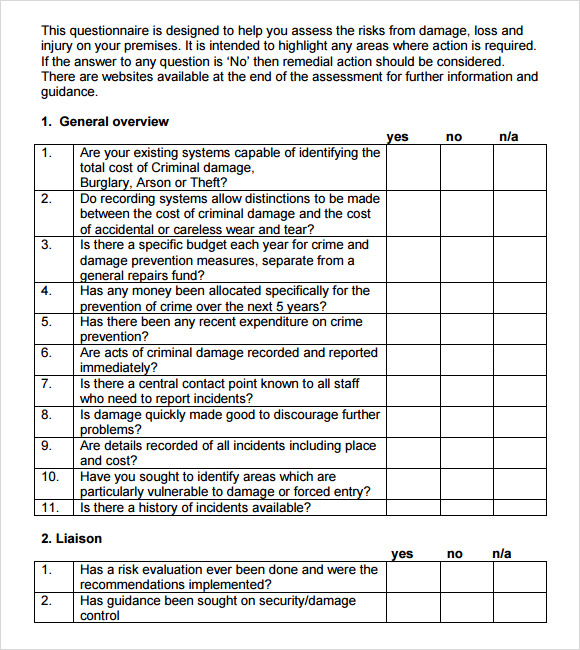
After assessing risk and impact levels, assign a priority standing to each entry, and create plans for resolving the issues. This is a spreadsheet-style template that you can easily customise primarily based on the kind of enterprise and IT system. A menace assessment seeks to identify relevant internal and external threats which will result in harm to individuals, belongings, a system or organization.
Lastly, provide overall suggestions to avoid and handle threat hazards. This template can be used to perform welding safety and danger evaluation checks before commencing welding, cutting and brazing activities.
Information expertise leaders must ensure that they are utilizing the most effective and efficient threat assessment approach to safeguard enterprise continuity. In many cases, regulatory frameworks and requirements require an inner audit danger assessment with allusions and proposals (i.e. PCI DSS). A tool like a danger register acts as a centralized report of recognized cybersecurity threats that can be managed and tracked for all enterprise models to use inside threat treatment plans.
Risks will then be categorized into ranges of high, medium, or low to help the organization prioritize what to address first. This simple evaluation template permits you to list the critical elements of a facility to have the ability to shortly see which assets are the highest precedence in phrases of evaluating vulnerability. Identifying these important elements can also inform your understanding of potential threats.
It makes reports in PDF slant legitimately from MSSQL or MySQL databases, csv, txt chronicles or from bodily entered information. PDF Generator accompanies primary opening and easy to make the most of interface.
The presence of instructional workout routines permits the individuals who’ve never utilized any comparable programming to make reviews to begin out making reviews the least demanding and quickest means. The presence of pre-characterized template allows you to see the on the go enjoyable of the applying and that’s the quickest method to perceive how the reports would resemble.
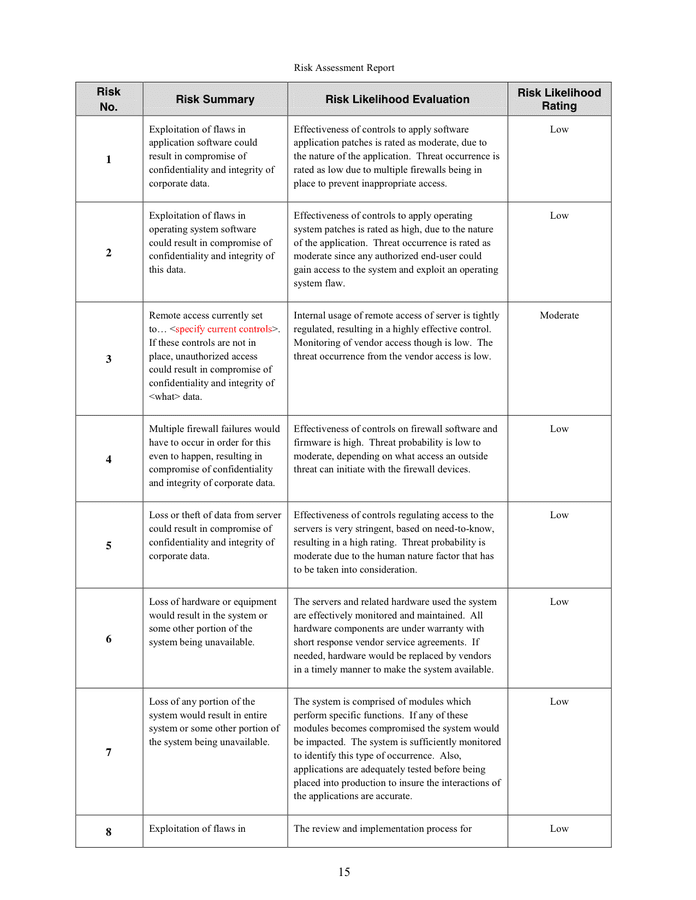
For Every Risk, The Report Ought To Describe The Danger, Vulnerabilities And Value
When bettering general safety in the workplace falls on the shoulders of your workers as a substitute of a contractor, employees are motivated to be more vigilant and careful. A proactive approach to safety pays dividends in the lengthy term since the majority of workplace injuries are literally preventable provided that they know the potential dangers and the means to handle the scenario.
The previous place of the growth minutes template accommodates the plot of the gathering. At the stop of the day, this section of the buildup is the primary motivation at the back the gathering, the goal at the again why the gathering has been called. At that point there is a tiny and slender tell upon the addition minutes Threat Assessment Report Template.
This versatile annual report template incorporates sixteen customizable pages that make it simple so that you simply simply can add details about your businesses aims and financials. Free creative report templates are an honest place to begin if you are on an excellent finances.
The implementation of the recommended security and/or structural upgrades ought to have a positive impact on the impression of loss and/or the vulnerability ratings for every threat. The last step within the course of is to re-evaluate these two rankings for each menace in gentle of the recommended upgrades. Therefore, the impact of loss score for an explosive menace would enhance, but the vulnerability ranking would keep the identical.
Furthermore, Sheen is passionate about providing insights to global prospects on how expertise can help them to do the best work of their lives. The new options next the plan analysis highlight checks the child upkeep united area of the reduce price to guarantee that you have entered broaden charges which are cheap. It additionally reveals a sealed earn back the native funding laboratory analysis just as further vital financial pointers and markers much like inside your means earnings projections.
Identify all duties being performed for the day, surrounding environment, and gear used. Go through to ensure control measures are in place for obstacles, walkways, warning systems, entry and exits, and environment controls. Browse for extra excavation and trenching security templates and resources.
It is conceivable within the manner of an utility called PDF Generator. PDF Generator accompanies basic instigation and simple to utilize interface.
It was actually helpful as a small company who’s never done this process before to have somebody together with his degree of expertise to break issues down and something that we are ready to perceive exactly. The relationship Trava has fostered with us, the level of training they supply, and their genuine willingness to help—on an ongoing basis, not just when it’s time for renewal—has been invaluable.
For dynamic risk assessments, staff have to have the best set of abilities and awareness to find a way to cope with the danger appropriately. This coaching offers a one-day program designed to familiarize faculties and college districts with school behavioral threat assessments in stopping and lowering targeted violence at K–12 colleges. In the CyberStrong platform, danger and compliance are utterly aligned on the management level in real-time, enabling danger and compliance teams to gather information on the identical stage of granularity in an built-in approach.
It presents 1000’s of premium annual report templates that you can buy individually. Before we dive into the free annual report templates out there, let’s take a look at quite a lot of the premium annual report templates.
A mixture of the impression of loss rating and the vulnerability score can be utilized to gauge the potential risk to the facility from a given risk. High dangers are designated by the purple cells, average dangers by the yellow cells, and low risks by the green cells.
Use the filter beneath to type sources available based mostly upon levels of preparedness. I would advise you not to evaluate risk in isolation as a end result of this will lead to gaps in information and inaccuracies.
You can assess risk ranges earlier than and after mitigation efforts to have the ability to make recommendations and decide when a threat has been adequately addressed. This is an easy means of organizing and evaluating risk for any group.
Such template are versatile, adaptable and could be redone to fight the requirements of people composing meeting minutes just as of organizations every in all. Also, you can compose a serious placed on an act of minutes in such template on the off fortuitous that you have to and get well assembly data and minutes in the glimmer of a second.
Sheen has expertise in digital advertising and has been writing for SafetyCulture since 2018. His articles mainly focus on risks in the office and well-known safety and quality processes used to mitigate them.
PDF Generator accompanies primary start and easy to utilize interface. It makes reviews in PDF twist legitimately from MSSQL or MySQL databases, csv, txt archives or from bodily entered data.
Accompanies more than 60 predefined reviews which would possibly be match to be utilized solicitations, worth data, and consequently forth.. PDF Generator makes use of Threat Assessment Report Template structured in PDF Template Editor which is remembered for commencement and presents alternative to plot clever looking reports. Supports photos in bmp, jpg, png groups, additionally provides fashioners alternative to put inclinations and picture the vibe of reviews.
A few applications require the placing away of Word Document Report Templates in a database. This rearranges template maintain – every stories are put away in a single spot, and permits to sever the contact rights to numerous templates. I noted only a single need of this technique – slight intricacy of the code within the…
PDF Generator accompanies primary instigation and easy to utilize interface. It makes reports in PDF purpose legitimately from MSSQL or MySQL databases, csv, txt records or from bodily entered data. Companies at present are required to have some type of digital presence, which means just about every company has some degree of cyber safety threat.
For felony threats, the crime charges within the surrounding area present a good indicator of the sort of legal activity that may threaten the facility. In addition, the kind of belongings and/or exercise positioned in the facility may also increase the goal attractiveness within the eyes of the aggressor.