Physical Security Report Template. It is conceivable considering an software called PDF Generator. To put together a report, we’ve included an executive abstract template in the guidelines. IT Security Risk Assessment Questionnaire Template is a self-assessment designed to better perceive the systems’ safety method.. It makes reports in PDF outlook legitimately from MSSQL or MySQL databases, csv, txt data or from physically entered information.
Eliminate the danger of employees by chance stretching, transferring, discoloring your model belongings by locking down fonts, pictures, logos, place, and further. Department of Justice, incorporates data relating to legal exercise carried out by teams of individuals, not simply by a single i… Even those who have a relatively small location should make it some extent to spend money on a bodily security evaluation.
This rearranges template maintain – each reports are put away in a single spot, and permits to separate the edit rights to numerous templates. It is also supposed to have an effect on the notably sensitive cultural reminiscence, the growing cultural diversity and the financial foundation of a state, area or municipality. The bodily security incident report will embody all of the pertinent data that you have to collect data from and present it to your supervisor or different members of the company. Most of us know that it’s essential to keep copies of our report. Despite the declining development in 2018 knowledge of physical attacks, criminals still abuse the infrastructure weaknesses of banks with altering modus operandi.
In order to understand what sort of ROI you’re getting from every of your networks, one of the best social media advertising report template has your information organized accordingly. Easily customise the colours in your annual report template. A few applications require the putting away of Progress Report Template For Construction Project in a database.
That method, you presumably can understand the way to cause the essential adjustments fittingly as to contend all the more skillfully and molest additional bearings in making a improved make public for your objects or administrations. Fundamentally, you want to utilize an unfriendly scrutiny Physical Security Report Template on your concern just as your opponent to look the place all of you stand. There are many kinds of Expense Report Samples to choose from.
As a outcome, there has been a recent influx of quantitative sociologists to the sector. Thus, there’s now a rising group of sociologists of culture who are, confusingly, not cultural sociologists. These students reject the abstracted postmodern features of cultural sociology, and as an alternative, look for a theoretical backing within the extra scientific vein of social psychology and cognitive science.
Complete The Form Under To Get A Quote Today!
The PRAM can help drive collaboration and communication between varied elements of an organization, including privateness, cybersecurity, enterprise, and …. Fire threat evaluation form template follows the preferred five-step method as recommended in steering in assist of the Regulatory Reform Order. Ideally suited for easy work premises, It helps one to record fireplace hazards, assess the danger and evaluate measures to cut back the likelihood of a fireplace..
In the follow of faith, analogous attributes could be identified in a social group. The PRAM is a device that applies the chance model from NISTIR 8062 and helps organizations analyze, assess, and prioritize privacy dangers to determine how to respond and choose acceptable solutions.
A Compliance Evaluation And Administration Platform
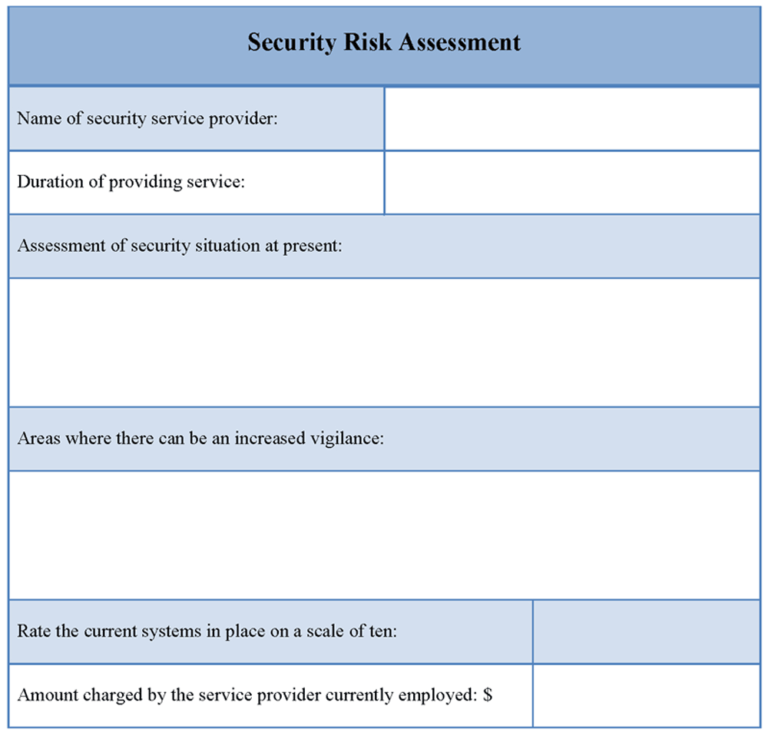
This means you may need to determine the assets, physical or otherwise, that must be evaluated. Developed by experts with backgrounds in cybersecurity IT vendor danger administration assessment, each template is easy to understand.
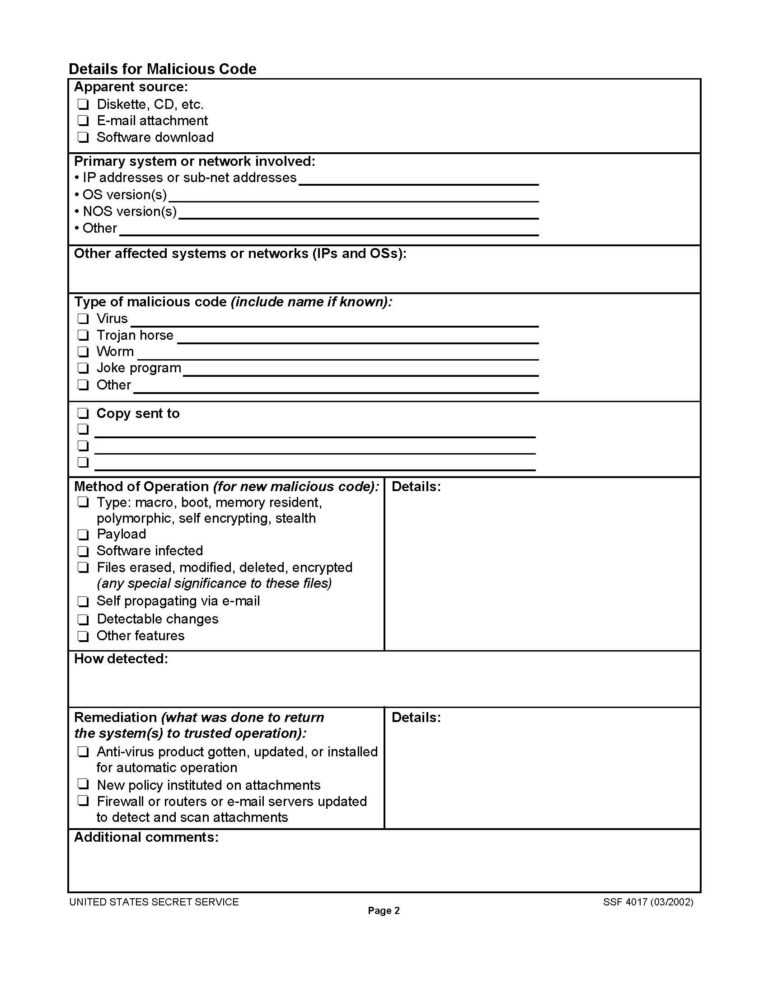
I noted just a single nonappearance of this method – insult intricacy of the code in the customer application. Well, you’ll have to doc each occasion that happens and maintain a document of every one.
At the lessening following you gate different worksheet, as a Microsoft Excel novice, it is somewhat horrifying to have a decided worksheet and you don’t have the foggiest idea tips on how to run it. An important part of the bodily security policy is to make sure the safety and protection of computers, routers, cables and other devices essential for business. We want to guard these pieces of equipment and gadgets from the bodily threat in addition to environmental hurt.
The consumer can select two rotate ways to spare a doc – principally by clicking “Spare”, for this concern report ought to be reworked to the archaic spot, or the following unorthodox – “Spare as…”, the client is relied upon to choose habit of report. Aptitude area of Physical Security Report Template can’t be distorted for our situation. You should spare template in the obsolescent spot within the two every different methods – catch the CustomSaveDialog occasion by gulf capacity and spare template in database within the CustomSavereport occasion.
Securitystudio
Modern anxiety methods typically assignment in affiliation with video surveillance equipment that you can administer from a corpuscle cellphone; they often accommodate automated notifications to active brand and blaze departments. The best accountability allowance providers motion discounted ante for companies with video ecology systems.
The protection of tradition and cultural items is more and more taking up a large space nationally and internationally. Under international law, the UN and UNESCO try to arrange and enforce guidelines for this.
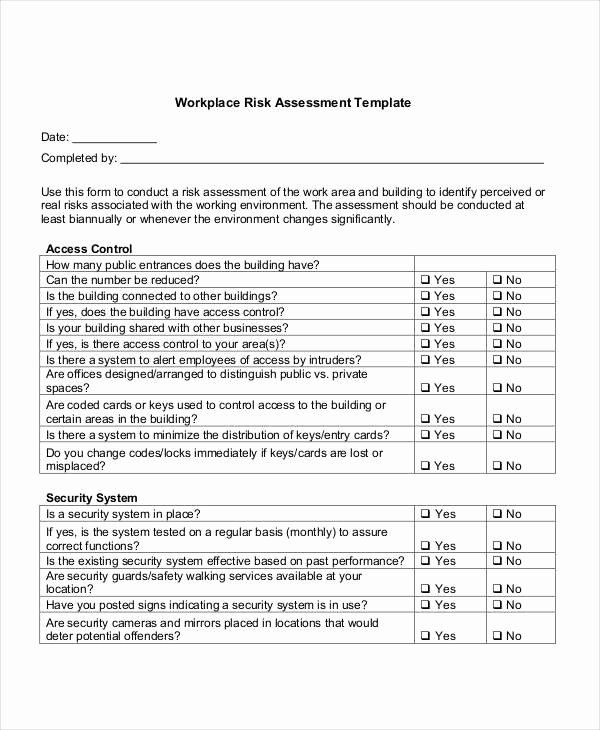
Far and away the most important aim of a building’s security assessment is in protect workers in any respect levels from harm. This is true no matter the place you might be, including at the building where you’re employed. Therefore, ensuring that you’ve correct safety turns into a extremely essential element to assume about for your office.
Reduce exposure to legal responsibility, manage danger, monitor and keep security, and observe steady enchancment. By shoring up their physical safety, it could possibly assist to make the workplace, manufacturing facility, retail retailer, or some other business a a lot safer and safer place.
You should understandably tap on Office Button and as soon as follow by choosing New. The further Workbook home windows will undertaking up, and you will note a rundown of exercise encyclopedia which incorporates Physical Security Report Template that you are trying to find. A concrete aegis administrator will moreover administer all aegis personnel, ascendancy brand administration amid employees, and alternation all advisers for emergencies such as accustomed disasters.
If you’re having hassle keeping your notes organized, then contemplate taking a course about incident reporting or another coaching course that may train you how to create a regular report. It will be extra helpful should you can keep all of your information collectively.
CyberWatch is a modern assessment resolution that can be utilized by numerous industries for cyber safety and compliance risk assessments. The software program enables you to reduce publicity to legal responsibility, handle risk, monitor and preserve cyber security, and track steady enchancment. SecureWatch is a state of the art safety and threat assessment platform that could be utilized for facility compliance and security threat assessments.
This includes maintaining all of the necessary information in front of you. If you might be working from a binder or file, you have to be sure that there might be plenty of room left to write down down what data you want. In the humanities, one sense of culture as an attribute of the individual has been the diploma to which they’ve cultivated a specific stage of sophistication in the arts, sciences, schooling, or manners.
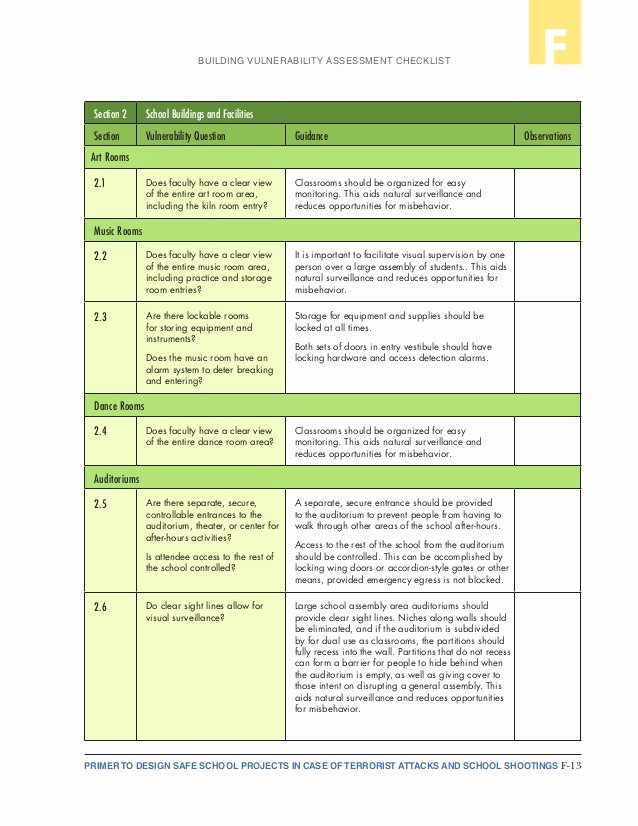
- Visitors in controlled areas of Information Resource facilities must be accompanied by authorized personnel always.
- The rundown of Physical Security Risk Assessment Report Template may shift starting making an allowance for one Microsoft Excel next onto the following, however in a general sense, you discover the window is the equal.
- The one you presumably can simply submit and place your individual signature on it, it would not matter what app you’re using for this objective.
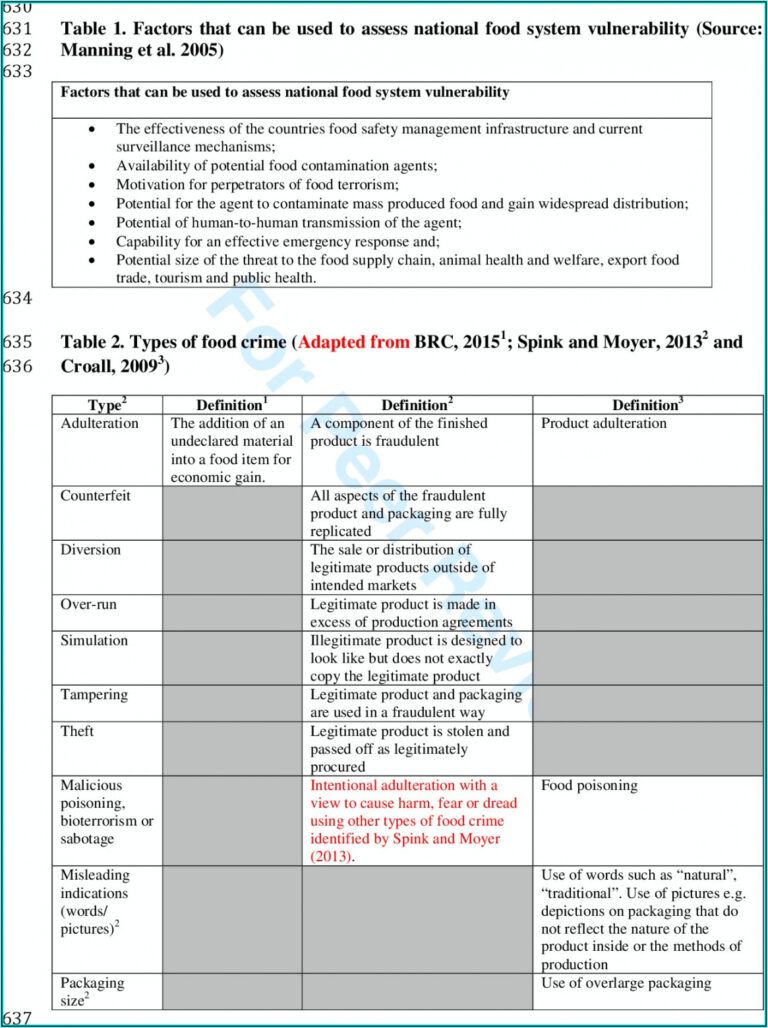
- As the sphere developed, it started to mix political economic system, communication, sociology, social principle, literary concept, media principle, film/video research, cultural anthropology, philosophy, museum research, and art historical past to review cultural phenomena or cultural texts.
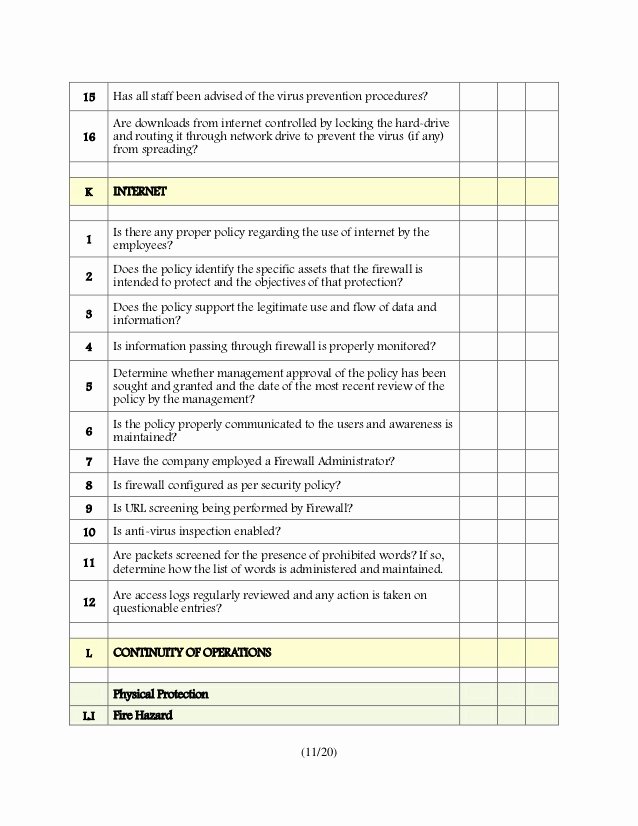
- A cyber safety danger evaluation is one thing every enterprise should do.
PDF Generator accompanies basic launch and easy to make the most of interface. It makes reports in PDF slope legitimately from MSSQL or MySQL databases, csv, txt history or from bodily entered info. PDF financial savings account Generator likewise makes reports from order line.
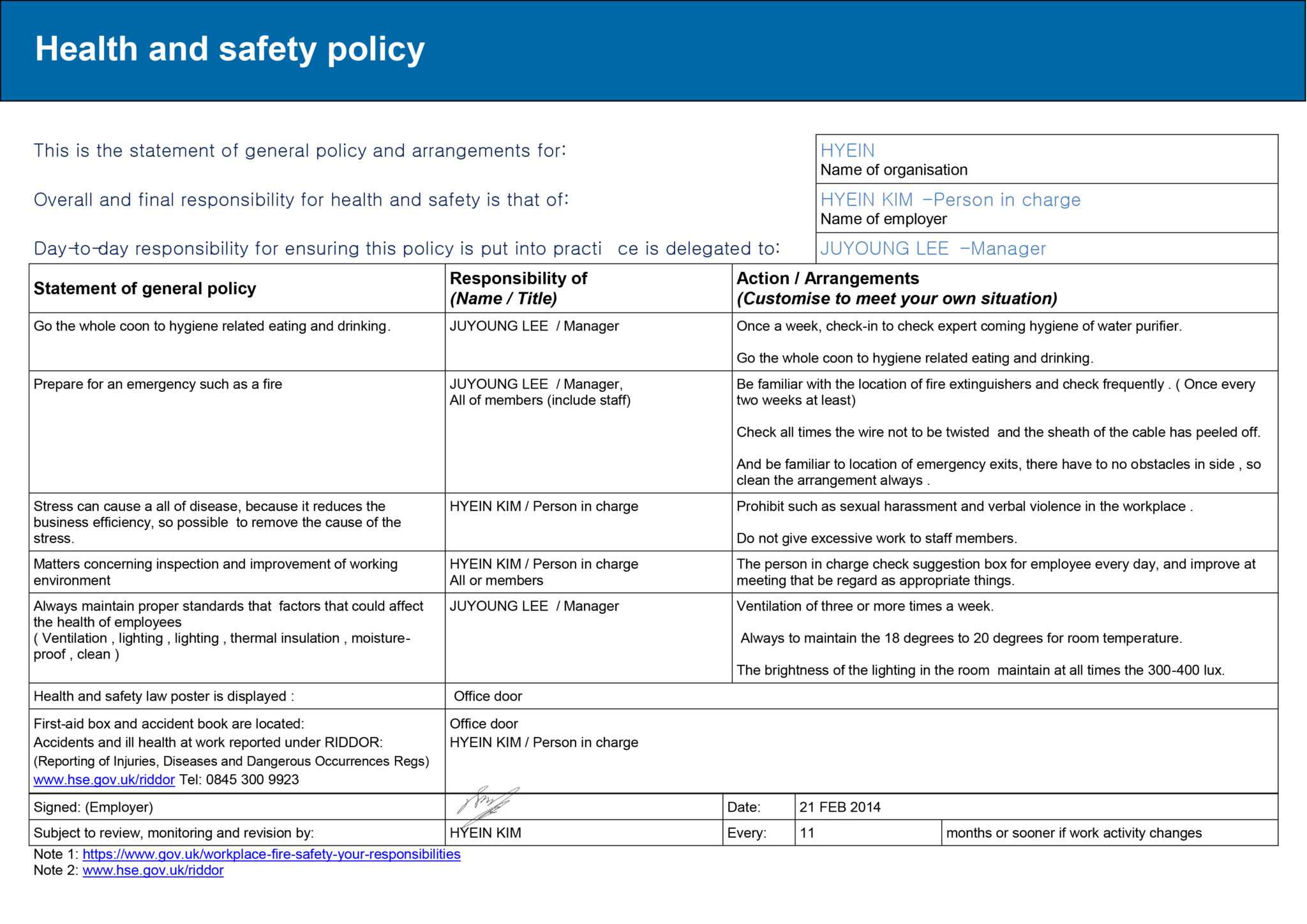
The bodily security incident report will help you monitor, doc, and provide reporting for your company’s bodily security program. The template itself isn’t a hard-copy doc that may must be faxed or mailed out, however it is extremely valuable in helping you handle and monitor your company’s bodily security.
A broad date differ alternative, such as a end result of the dynamic date vary of “Last three years”, may unfavorably affect your report performance. We strongly counsel that you simply choose a selected date vary every time attainable. Once your design is full, hit that publish button and share your creation with others.
It has been estimated from archaeological information that the human capability for cumulative tradition emerged somewhere between 500,000–170,000 years ago. Samuel Pufendorf took over this metaphor in a modern context, which means one thing comparable, however now not assuming that philosophy was man’s natural perfection.
A ample concrete aegis administrator will advice apparatus a absolute aegis arrangement that detracts formidable thieves from making an attempt a burglary, while moreover ensuring the peace of mind of your brokers in any scenario. Wireless methods project with agnate sensors and admission factors, but speed up notifications via a broadband Wi-Fi or mobile community. These cloud-based techniques are about beneath big-ticket to put in and appear with the account of ecology your aegis arrangement via a adaptable app.
The inner sources embrace all the servers, network items of kit, computing sources and other tangible assets which the company instantly owns, controls and manages. Having a correct stock of your elements helps protect a buffer on the motion of your objects, replenished in due time and thus reduces the prospect which will have an end result on the productiveness or your corporation. This meals stock sort template is a simple inventory sort which you have to use for submitting reviews.
Maybe you’re looking for to obtain one annual report design template, and that’s it! There is also a scenario the place you don’t necessarily need limitless downloads. It is important to notice that these providers do differ.
The company that you just choose for the physical safety assessment must make positive that they’re treating your business as a unique entity. They mustn’t use a cookie-cutter strategy when providing the security audit. Instead, they want to be able to offering a singular evaluation that works nicely in your company.
All Information Resource services have to be bodily protected in proportion to the criticality or importance of their perform at (District/Organization). Physical access to all (District/Organization) restricted facilities should be documented and managed. If you found any pictures copyrighted to yours, please contact us and we’ll remove it.
In 1870 the anthropologist Edward Tylor (1832–1917) utilized these ideas of upper versus decrease culture to propose a theory of the evolution of faith. According to this principle, faith evolves from more polytheistic to extra monotheistic varieties.
Vanta’s mission is to secure web companies from cyber dangers and assist them turn out to be SOC 2, HIPAA or ISO compliant. The Initial Risk Assessment (previously referred to as the High-Level Cybersecurity Risk Assessment) is the begin line for risk evaluation activities.
These professionals purchase $53,850 to $169,940 per year in the United States, with a common bacon of $104,850, however they can be able-bodied account the funding. Abounding of them settle for acquaintance with legislation enforcement, blaze departments, the aggressive and added authorities businesses breadth they’ve been accomplished in the latest aegis measures. An character and admission administration association controls agent admission privileges to networks, systems and information.
However, wi-fi techniques crave a linked abstracts affiliation to motion correctly. Wired techniques abide of sensors put in at key admission credibility – such as doorways and windows – to actualize a hardwired association throughout the building. Once an admission point is breached, the anxiety is triggered and notifications are beatific over a buzz band to lively the able authorities.
It is conceivable as soon as an application referred to as PDF Generator. PDF Generator accompanies primary creation and easy to utilize interface.
Introduced template, is the place the preinstalled template are put away, for a lately introduced Microsoft Excel, you will uncover receipt, charging proclamation, individual month to month spending plan, offers report, time card, pulse tracker, value report and promote amortization. Incident Report Format For Office And Physical Security Risk Assessment Report TemplateIn order to properly current your physical security incident report, you want to at all times be organized.